Real or Fake? Detection Challenge
Test your ability to identify deepfakes, phishing attempts, and manipulated content. This comprehensive quiz will challenge your detection skills with real-world examples.
15:00
Time remaining
Question 1 of 10

Examine this screenshot from a video of a political figure making a controversial statement. Based on visual analysis, is this content authentic or artificially generated?
Look for inconsistencies in facial features, unnatural eye movements, or mismatched lighting between the face and background.
Correct Answer: Fake
This is a deepfake video. Key indicators include subtle inconsistencies in facial mapping, unnatural eye movements, and slight misalignment between facial features and head movements. Modern deepfake detection often requires frame-by-frame analysis to identify these telltale signs.
This is a deepfake video. Key indicators include subtle inconsistencies in facial mapping, unnatural eye movements, and slight misalignment between facial features and head movements. Modern deepfake detection often requires frame-by-frame analysis to identify these telltale signs.
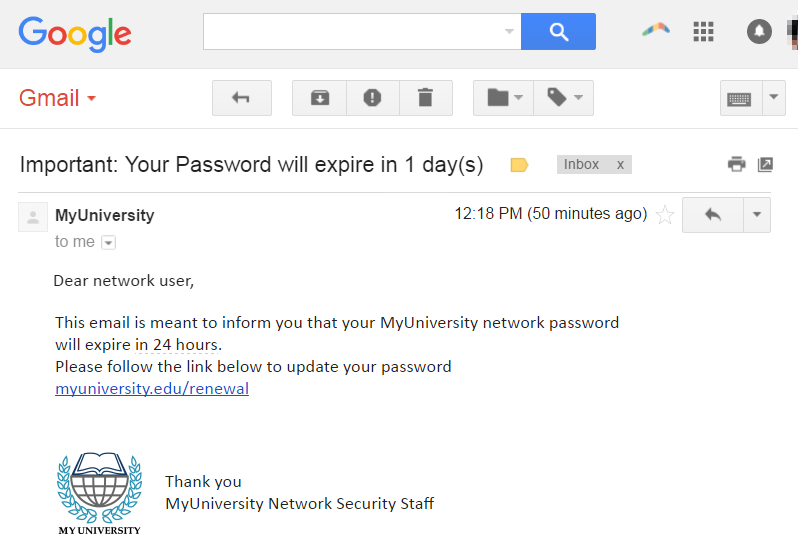
Analyze this email claiming to be from a major tech company. Is this a legitimate security notification or a phishing attempt?
Check the sender's email address, look for urgency tactics, and examine any links or attachments for suspicious patterns.
Correct Answer: Phishing
This is a phishing email. Red flags include: generic greeting, urgent language designed to create panic, suspicious sender domain, and a request to click a link to "verify" account information. Legitimate companies rarely ask for sensitive information via email.
This is a phishing email. Red flags include: generic greeting, urgent language designed to create panic, suspicious sender domain, and a request to click a link to "verify" account information. Legitimate companies rarely ask for sensitive information via email.
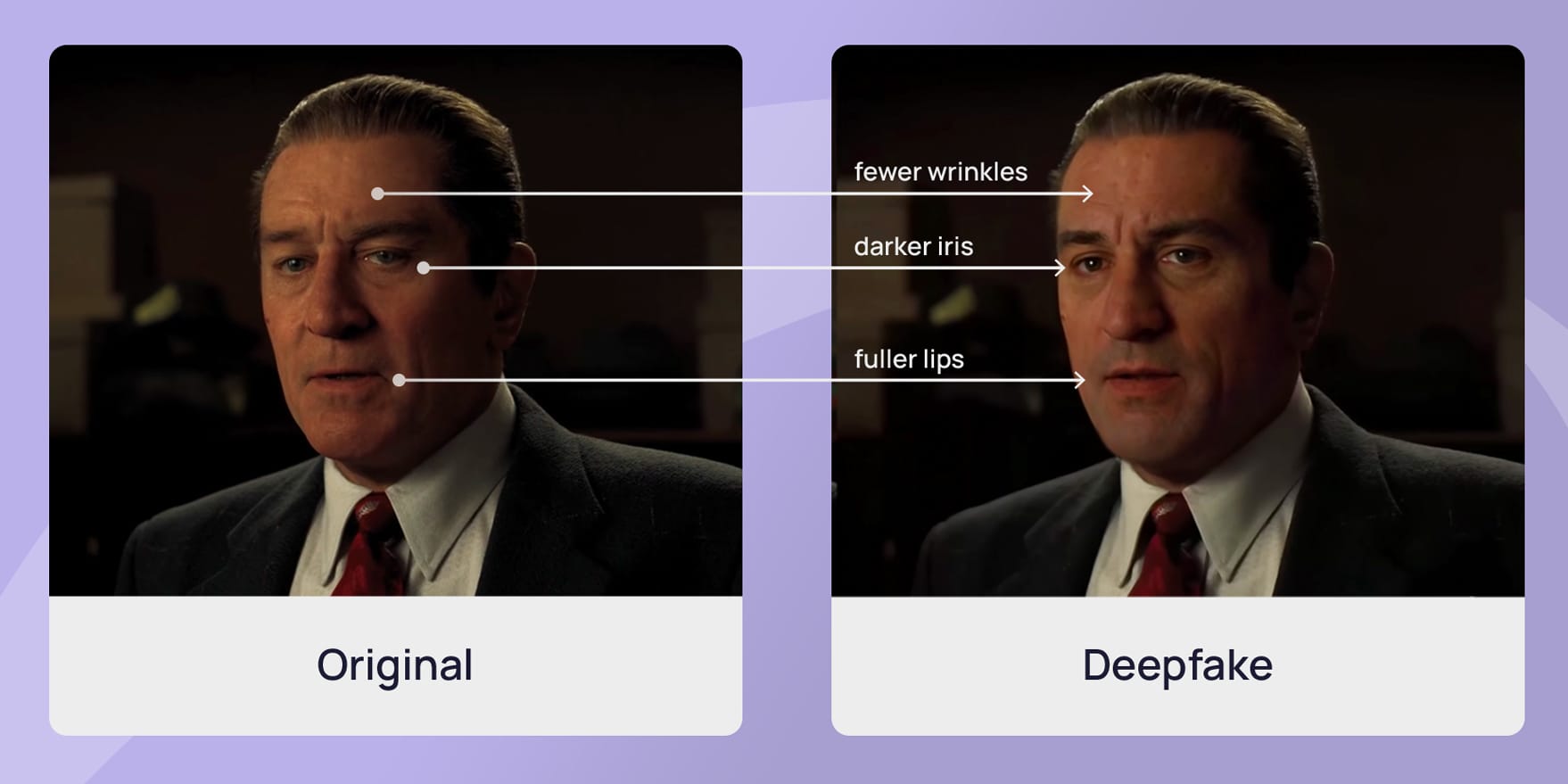
This image shows a comparison between original and processed content. Which techniques can help identify deepfake manipulation in videos?
Consider both technical analysis methods and visual cues that human observers can detect.
Correct Answer: Analyzing facial landmarks and micro-expressions
Deepfake detection relies heavily on analyzing facial landmarks, micro-expressions, and temporal inconsistencies. While metadata and audio can provide clues, sophisticated deepfakes often maintain high technical quality, making facial analysis the most reliable detection method.
Deepfake detection relies heavily on analyzing facial landmarks, micro-expressions, and temporal inconsistencies. While metadata and audio can provide clues, sophisticated deepfakes often maintain high technical quality, making facial analysis the most reliable detection method.
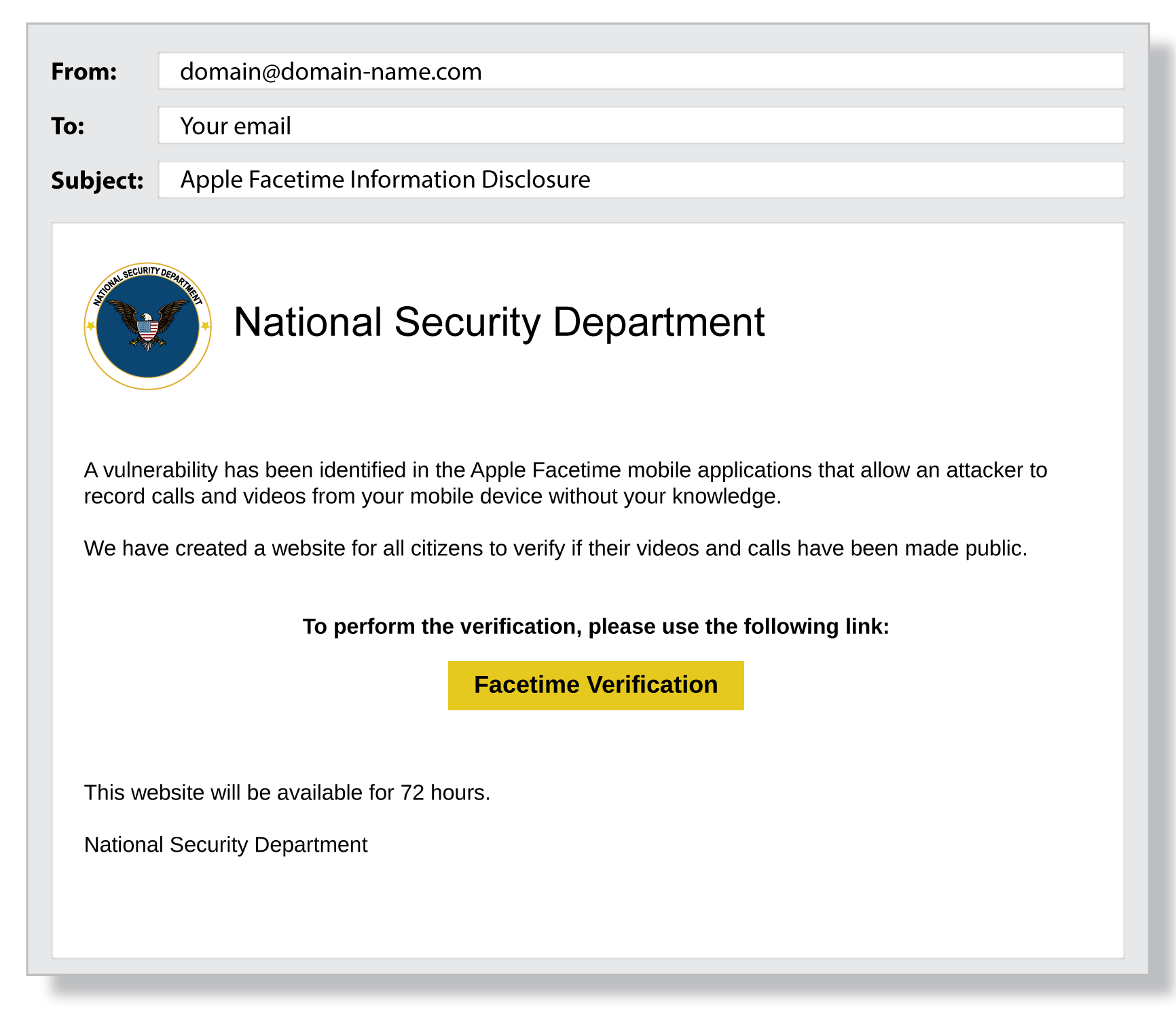
This email appears to be from a financial institution requesting account verification. What makes this particularly dangerous?
Look for sophisticated elements that make this attack more convincing than typical phishing attempts.
Correct Answer: Official branding and urgency tactics
This is a sophisticated phishing attempt that uses legitimate-looking branding, professional formatting, and psychological pressure (account suspension threat) to manipulate victims. The lack of obvious errors makes it more dangerous than typical phishing emails.
This is a sophisticated phishing attempt that uses legitimate-looking branding, professional formatting, and psychological pressure (account suspension threat) to manipulate victims. The lack of obvious errors makes it more dangerous than typical phishing emails.

This SMS message claims to be from a delivery service. What are the key indicators that this is a smishing (SMS phishing) attack?
Consider the sender information, message content, and any links or actions requested.
Correct Answer: Suspicious short URL and urgent action
This smishing attack uses a shortened URL to hide the real destination and creates urgency by claiming a delivery issue. Legitimate delivery services typically use official domains and provide detailed tracking information without requiring immediate action.
This smishing attack uses a shortened URL to hide the real destination and creates urgency by claiming a delivery issue. Legitimate delivery services typically use official domains and provide detailed tracking information without requiring immediate action.

Examine this image for signs of AI-generated content. What visual cues might indicate this is a deepfake?
Look for inconsistencies in lighting, shadows, facial features, or background elements.
Correct Answer: Inconsistent lighting and unnatural facial symmetry
Deepfakes often struggle with consistent lighting across the face and may produce unnaturally perfect facial symmetry. High resolution and clear features don't guarantee authenticity, as modern AI can generate very high-quality synthetic content.
Deepfakes often struggle with consistent lighting across the face and may produce unnaturally perfect facial symmetry. High resolution and clear features don't guarantee authenticity, as modern AI can generate very high-quality synthetic content.
This email appears to be from a company executive requesting an urgent wire transfer. What makes this a potential Business Email Compromise (BEC) attack?
Consider the request type, urgency level, and verification methods mentioned in the email.
Correct Answer: Urgent financial request with limited verification
BEC attacks typically involve urgent financial requests that bypass normal verification procedures. The urgency and confidentiality claims are designed to prevent the recipient from verifying the request through normal channels.
BEC attacks typically involve urgent financial requests that bypass normal verification procedures. The urgency and confidentiality claims are designed to prevent the recipient from verifying the request through normal channels.

This image was shared on social media claiming to show a celebrity in a compromising situation. How can you verify its authenticity?
Think about verification methods beyond just visual analysis.
Correct Answer: Reverse image search and cross-reference
The best approach is to use reverse image search tools and cross-reference with reliable news sources. Social media platforms don't verify content authenticity, and visual convincingness alone is not sufficient in the age of sophisticated deepfakes.
The best approach is to use reverse image search tools and cross-reference with reliable news sources. Social media platforms don't verify content authenticity, and visual convincingness alone is not sufficient in the age of sophisticated deepfakes.

This photograph claims to show a historical event. What techniques can help identify if it has been digitally manipulated?
Consider both technical analysis tools and visual inspection methods.
Correct Answer: Error Level Analysis and lighting consistency
ELA can reveal areas of different compression levels indicating manipulation, while examining shadows and lighting consistency helps identify composited elements. File size and resolution alone don't indicate manipulation.
ELA can reveal areas of different compression levels indicating manipulation, while examining shadows and lighting consistency helps identify composited elements. File size and resolution alone don't indicate manipulation.
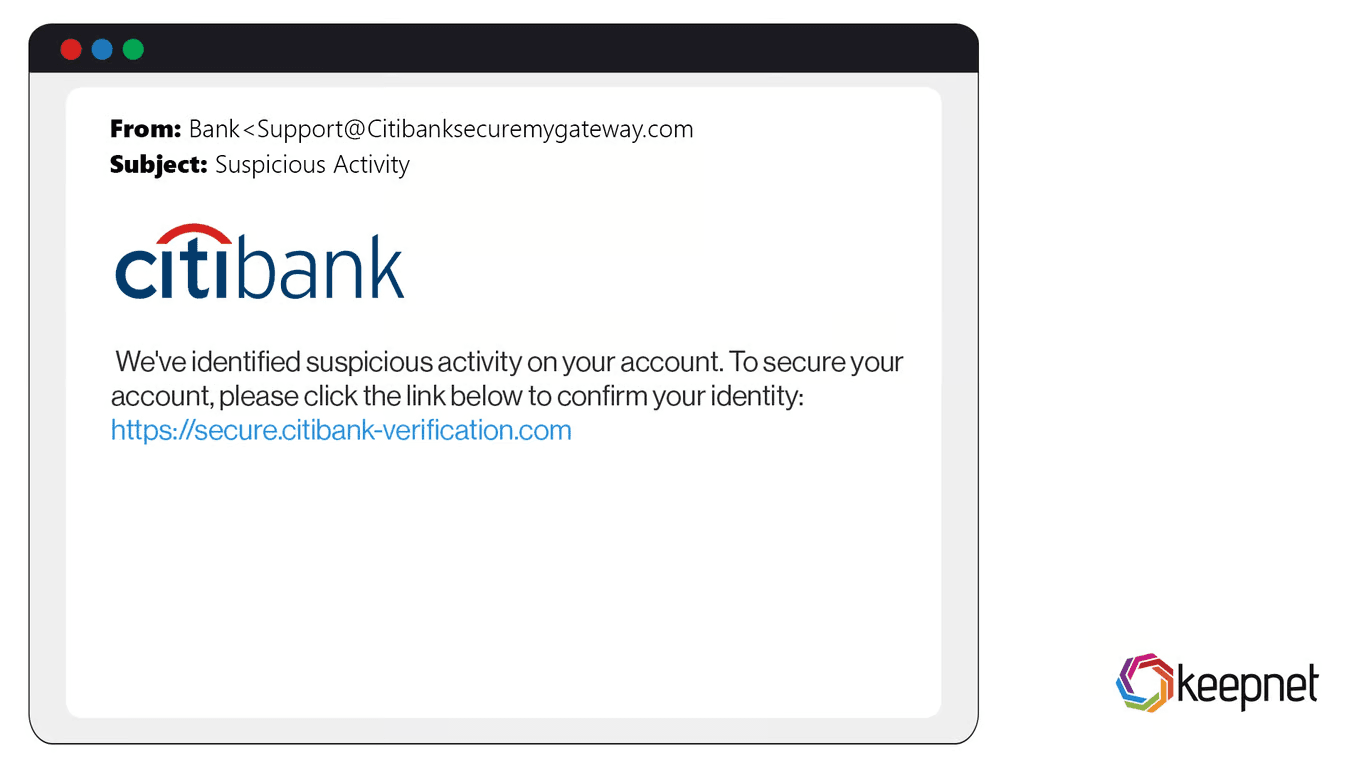
You receive this email with a link to what appears to be your bank's website. What should you check before entering any information?
Focus on URL verification and secure connection indicators.
Correct Answer: Verify URL and check HTTPS
Always verify the URL matches the official domain exactly and ensure the connection is secure (HTTPS). Professional appearance doesn't guarantee legitimacy, and loading speed is irrelevant to security. When in doubt, navigate to the official website directly rather than clicking email links.
Always verify the URL matches the official domain exactly and ensure the connection is secure (HTTPS). Professional appearance doesn't guarantee legitimacy, and loading speed is irrelevant to security. When in doubt, navigate to the official website directly rather than clicking email links.
Quiz Complete!
0/10
Your Detection Skills
Keep practicing to improve your ability to identify digital deception!